
Black Box vs. Grey Box Penetration Testing
In the cybersecurity landscape, penetration testing is a critical component of an organization’s security framework. Among the various types of penetration testing, Black Box and
Manage Vulnerabilities, Discover IT assets, Scan Web Apps, Inventory Cloud Assets.
Experience hassle-free and cost-effective penetration testing for an array of compiance standards!
Stay ahead of potential threats with our application and cloud vulnerability management services. We offer Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), Software Composition Analysis (SCA), Infrastructure as Code (IaC) assessments, and Container Scanning to keep your applications secure from every angle.
Safeguard your infrastructure with our comprehensive vulnerability management solutions. We provide internal and external vulnerability assessments to identify and address weaknesses in your systems, ensuring your organization’s digital assets are resilient against evolving threats.
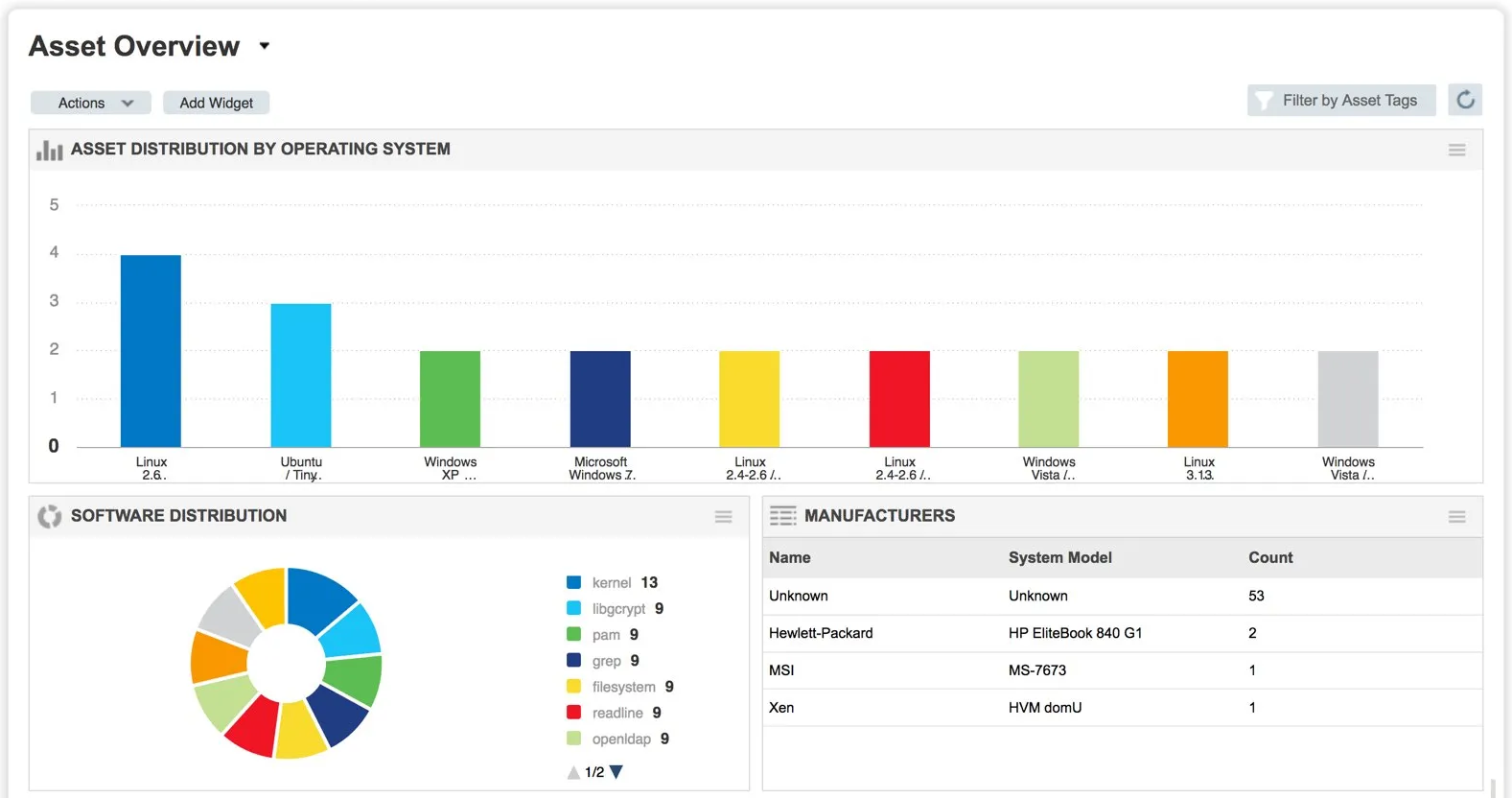
Discover your IT assets and their vulnerabilities, identify compliance gaps and get detailed reports using the industry’s most accurate and comprehensive security assessment tools.
We handle the entire Web, Application, Infrastructure, and API Penetration Testing process, from scoping, to final report delivery, and remediation planning. Book a Free Consultation
Free 8-in-1 online Application & Web vulnerability scanner that supports both external (DAST) and internal application scanning (SAST, SCA), Cloud Security Posture Management + More..
Premium 8-in-1 online Application & Web Vulnerability Scanner that supports both external (DAST) and internal application scanning (SAST, SCA), Cloud Security Posture Management + More..
Comprehensive online Risk-Based Vulnerability Management, Patching and EDR solution. Unlimited Internal and External scanning from $180/month.

External network, web, application, and API – Vulnerability Scanning is essential for all compliance frameworks (ISO 27001, SOC 2, PCI DSS, NIST, HITRUST, etc.). Our VM scanners reporting options not only help you meet your compliance requirements and satisfy your auditing team but also enhance your security posture, benefiting your organization and clients.
Compliance frameworks:





Typically, it's 3-5 times more cost-effective than comparable solutions. Reduce management overhead by using one dashboard for eight scanners!
Assessments for the entirety of the OWASP Top 10 Most Critical Web Application Security Risks.
Save up to 80% of your engineering resources by focusing on actual vulnerabilities, instead of chasing noise!
Test reports showing compliance with SOC 2, ISO 27001, OWASP Top 10 and CIS.
Integrate and connect directly with your current infrastructure. Supports major container registries, repositories, issue trackers, and more.
Enhance your security posture with a cloud security posture management module. Scan all of your cloud infrastructure in: AWS, GCP and Azure.
Connect your task management, messaging tool, compliance suite & CI to track & solve issues in the tools you already use.
We provide free support and assistance exclusively conducted by US-based engineers.
Typically, it's 2-3 times more cost-effective than comparable solutions. Consolidate Vulnerability Management, Patching and EDR in 1 solution.
Know all assets on-prem or cloud, and classify them based OS, application and 100+ attributes.
Detect critical threats up to 5x faster by leveraging Risk-Based Prioritization using 25+ threat intelligence feeds.
Automatically detect vulnerabilities in real time. Leverage auto patching to extend remediation and patch vulnerabilities up to 40% faster than other solutions.
Automatically block malware and ransomware infections. Set and forget patching to automatically remediate ransomware, and malware exploitable vulnerabilities.
Consolidate IT and Security Tools for vulnerability assessment, remediation and ransomware protection
Detailed reports meet the requirements for SOC 2, ISO 27001, PCI DSS, GDPR, HITRUST.
We provide free support and assistance exclusively conducted by US-based engineers.
As a burgeoning e-commerce company, the security of our customer data is our top priority. The team at PTG provided us with an incredibly thorough and professional penetration testing service. Their insights and recommendations were invaluable in strengthening our security posture. Their expertise, combined with outstanding customer service, makes them an indispensable partner in our security strategy.
Navigating compliance requirements was a daunting task for our healthcare startup. PenTestGurus not only pinpointed our system vulnerabilities with pinpoint accuracy but also adeptly guided us through the compliance process. The remediation support and follow-up services they provided were beyond our expectations. Our partnership with them is certainly one of the best business decisions we’ve made.
We were looking for a penetration testing service that could handle the complexity and scale of our financial services network. PenTestGurus exceeded our expectations in every aspect. Their meticulous attention to detail, coupled with cutting-edge testing methodologies, resulted in a comprehensive and actionable report. The level of expertise and professionalism they brought to the table was exemplary. I can confidently recommend them for any organization that takes security seriously.
Sign up for a Free Account / Trial, we will get back to you within 24 hours with the account details. You can also schedule a free consultation to learn more.
Vulnerability scanning is an automated process to identify known vulnerabilities in systems and applications. Penetration testing, on the other hand, is a more comprehensive and manual approach that simulates real-world attacks to identify both known and unknown vulnerabilities.
Initial account activation for most of our plans is less than 24 hours. You can start scanning immediately after your plan gets activated.
You can rely on our vulnerability scanning to meet all of your certification and audit requirements including: SOC 2, ISO 27001, NIST, HIPAA, HITRUST, PCI DSS, GDPR, CCPA, FedRamp, and SOX.
The frequency of the scanning depends on various factors such as the complexity of your infrastructure, compliance requirements, and the sensitivity of the data you handle. Generally, it is recommended to perform a Vulnerability Scan at least monthly.
We provide Vulnerability Management solutions for a diverse range of industries. Our experts are well-versed in various compliance frameworks, making us adept at catering to the unique needs and regulations of different sectors.
Vulnerability Management is a requirement for various compliance frameworks such as SOC 2, ISO 27001, HIPAA, and PCI DSS.
Absolutely! We offer specialized cloud security and vulnerability management services that will test your cloud environment.
To get started, reach out to us through the Book a Consultation or our quick sign up form. Our team of experts will be happy to discuss your requirements and guide you through the process.

In the cybersecurity landscape, penetration testing is a critical component of an organization’s security framework. Among the various types of penetration testing, Black Box and

Before diving deeper into the black box penetration testing cycle, it’s essential to understand how it differs from automated external vulnerability scanning. Though they share

Black box penetration testing is a method where testers evaluate the security of a network or system without any prior knowledge of its internal workings. This method closely simulates a real-world attack, as attackers usually do not have insider information.