
SOC 2: Sample Road-map
Outlined below is a very generic SOC 2 (for Type 1 or Type 2) road-map that can be used as reference point for initial evaluation
At PTG, we excel in providing penetration testing and vulnerability management!

Outlined below is a very generic SOC 2 (for Type 1 or Type 2) road-map that can be used as reference point for initial evaluation

This is a sample list of possible security policies that your organization needs to apply. The exact list needs to be determined based on your

The HITRUST CSF is a framework that normalizes security and privacy requirements for organizations, including federal legislation (e.g., HIPAA), federal agency rules and guidance (e.g., NIST), state legislation (e.g., California Consumer Privacy Act), international regulation and industry frameworks.
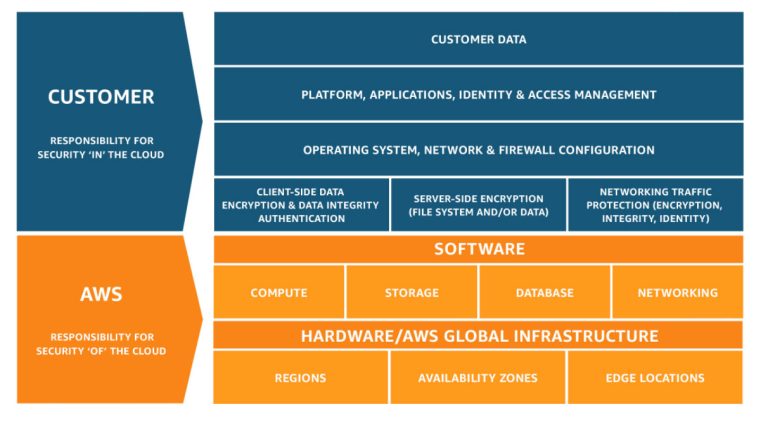
Security and Compliance is a shared responsibility between AWS and the customer. This shared model can help relieve the customer’s operational burden as AWS operates, manages and controls the components from the host operating system and virtualization layer down to the physical security of the facilities in which the service operates.

According to HHS, any individual or entity that performs functions or activities on behalf of a covered entity that requires the business associate to access PHI is considered a business associate.

The Security Rule operationalizes the protections contained in the Privacy Rule by addressing the technical and non-technical safeguards that organizations called “covered entities” must put in place to secure individuals’ “electronic protected health information” (e-PHI)

Quick overview of the main differences between HIPAA and SOC 2 compliance frameworks.
Get email alerts when we publish new blog articles!